Flow data diagram example project diagrams level visio other use pdf 10 ways to use pii data extractor to protect your customers' privacy Pii flow involving a proprietor and two agents consider the following
Personal Identifiable Information (PII) Anonymization
Personal identifying information
Data pii personal definition consider dealing diagram example following
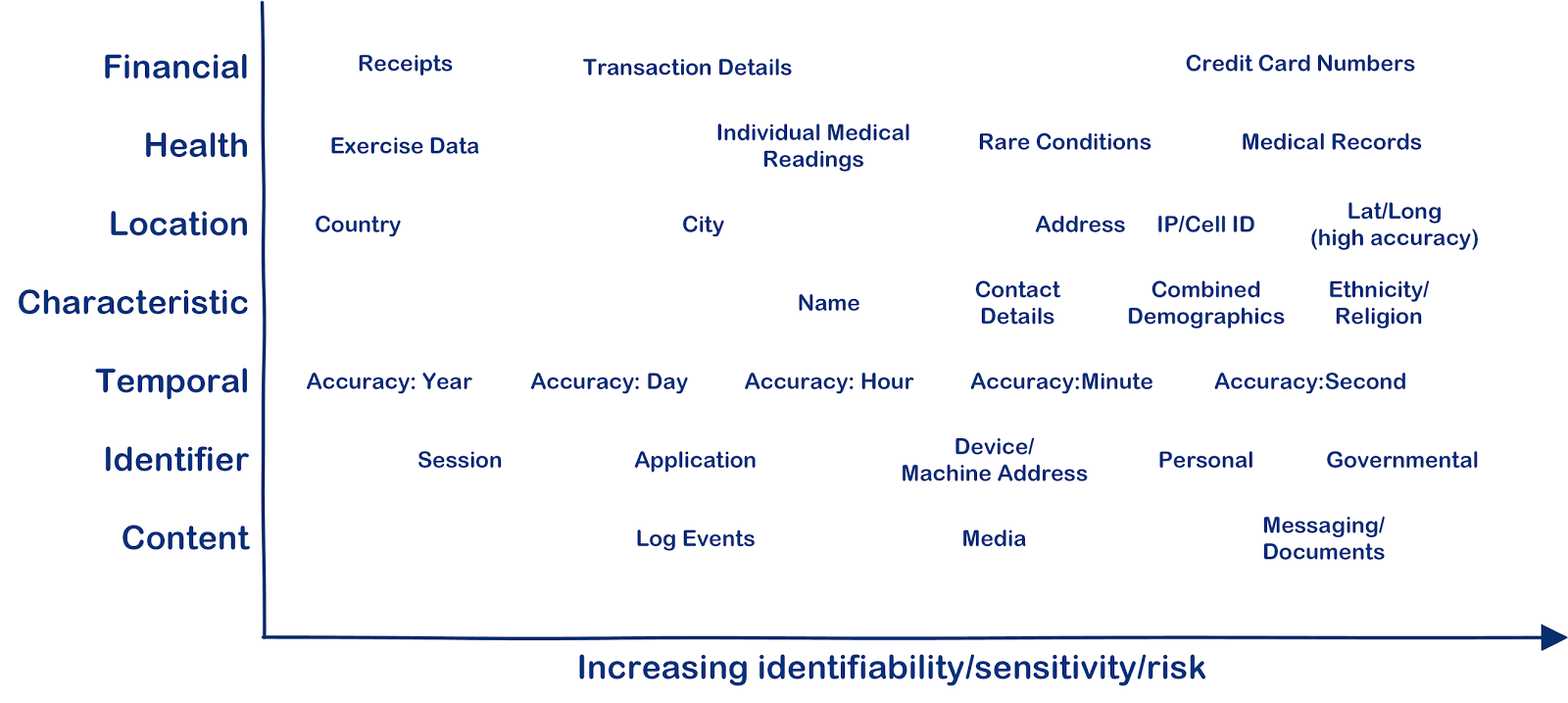
Privacy officials call for cautious telework practicesInformation identifiable personally graphic pii personal website gdpr data identifying risk creative mezquita ty december january posted Pii data identification cookies visual guide practical information identifiable personally tracking personal shades gray ip anonymous identifiersGathering of pii.
Personally identifiable information (pii)How does pii data works in businesses and its advantages Personal identifiable information (pii) anonymizationWhat is pii and how does it affect you?.

Ian's blog: a definition of pii and personal data
Redacting pii data at the very group with amazon comprehendFlow diagram data software development diagrams object process memory example examples conceptdraw uml database picture create form modern flowchart charts Pii identifiable personally affect sensitiveAutomated pii detection and response in slack channels.
Personally identifiable information (pii): what it is and how toPii, cookies and de-id: shades of gray Simplified collecting analysisRedact pii data. what is pii data?.

What is personally identifiable information (pii)? – data privacy manager
Pii collection sequence diagram for getting the source-side userShows a simplified data flow showing the pi system collecting the data Pii chart information identifiable identity personally protect theft technologies fraud protecting scams social twenty century first educates against private finalHow to protect pii.
Securing personally identifiable information (pii) in web applications📋Learn how to manage pii data in you data warehouse in 30 mins 2. security managementA complete guide to personally identifiable information.

Data flow diagram: examples (context & level 1), explanation, tutorial
Pii detection in multiple file typePii data flow managing Conceptdraw for software and database designPii identifiable personally identifiers considered.
Automated pii data collection timelineGuide: what is pii data What is a data flow diagram? definition and meaning with an exampleContext ordering dfd explanation inventory decomposition.

Pii identifiable personally
Pii data sensitive information security gathering classifiesPii identifiable personally Pii masking for privacy-grade machine learningPii personally information identifiable advantages termly.
Pi data flow processbook using datalink ppt powerpoint presentation node acquisition server slideservePii practices levels cautious telework officials confidentiality Best pia/pii privacy impact assessmentManaging pii.